Wednesday, March 30, 2005
NonoGrid and Canasta
I have owned a canasta game for many years created by Mark-Jan Harte from BP Games. It Is a great card game. He has now created a game called NonoGrid.
Nonograms are logic puzzles, in which you need to uncover a picture consisting of black and white squares. You start out with an empty grid and you use clues and logic to find out which squares in the grid should be black or white. The puzzle may have a title which can give you a clue as to what the final picture will be.
These puzzles originated in Japan and are very popular. Nonograms are known under many different names, e.g. griddlers, japanese puzzles, picture crossword puzzles or crosspix. Even Nintendo has created two nonogram games for the Gameboy, Mario's Picross and Picross 2.
Give them a go - if you like logic puzzles then these are definitely fun.
I have also been playing Magic Vines lately. This is a fun (and progressively hard) game. Also a great logic puzzle and great for a 10 minute break from coding.
Tuesday, March 29, 2005
Syndication
Great news!
I have been picked up by Robin Good from masternewmedia.org to have my content syndicated.
Watch this space for further news.
Thanks to Darren from ProBlogger for setting me on the right path.
Sunday, March 27, 2005
Jut when I thought I was clean - Hyperbar woes
Just when I thought I was clean - stupid jump tray.exe came back.
Well I cleaned out the exes agan - they had come back too.
Back in registry cleaner I cleaned again.
Then I went into the registry cleaner and searched for hyperbar and cleaned every single entry. Did the same for Startnow navigation helper.
Went to IE options and reset the defaults.
Now I think I am clean.
Igor (the programmer who wrote the hyperbar (that I don't remember installing - because I didn't) should be shot (slowly).
He has bypassed all the windows norms, it is effectively a virus as it is built to reporoduce itself constantly. It doesn't show in the Add remove programs box, though regcleaner finds it (but can't successfully remove it). He has hidden registry entries inside valid Microsoft registry keys and then forced changes to IE defaults such as search engines.
I will be monitoring closely over the next few days.
Prefetch, Stupid Jump Tray and Registry Cleans
It started with the system slowing, then freezing up all together. Admittedly I was running a lot of applications simultaneously, Excel, Outlook, Firefox, IE, ICQ, MSN, Dreamweaver, Photoshop, CuteFTP, Winamp and more. However the machine is a 3.2Ghz Intel Pentium 4 with 2 Gb of Golden Dragon Geil RAM. Should be able to cope - and usually did.
So I wondered why and went straight to the task manager to look.
Additionally I was trying to install Firefox 1.02 and after installing it the application wouldn't open, although its process was in task manager.
The first thing I noticed was that an application called stupid jump tray.exe was hogging all available CPU time. Whatever was spare it was taking and causing the CPU to run at 100%. Additionally an application called Build Program appeared now and again.
The first thing I assumed was that this was a trojan or virus of some sort. However scans revealed nothing.
Next I ran Adaware and then Spybot, free malware and spyware cleaner tools. While they picked up a few things they didn't fix this.
Next I ran RegCleaner and removed some applications I didnt need.
Still didn't fix it. A search on the hard drive for the file located it in the C:\Windows\Prefetch directory. I renamed it and it came back.
I opened msconfig and removed something called realbait.exe that was starting up when the PC started. Noting the location of this (Username\Application Data\ThisFirst) I discovered several exes including realbait, stupid jump tray and others. I deleted the entire directory.
I then searched in the registry and found it and removed the entire registry entry. It had attached itself to the Search Assistant.
Finally I googled C:\Windows\Prefetch and located a Prefetch cleaning tool on the Major Geeks Website. I downloaded and ran this (changing the Prefetch settings to Boot only as recommended by them).
Finally!
Success!
Clean - fast operating PC once more.
Saturday, March 26, 2005
CORRECTED: The power of Amazon Web Services
 I have resized the images in The power of Amazon Web Services and added a larger picture of the letter E. The images had been too large and was causing the navigation to the right to appear below the posts in Internet Explorer.
I have resized the images in The power of Amazon Web Services and added a larger picture of the letter E. The images had been too large and was causing the navigation to the right to appear below the posts in Internet Explorer.
Electronic Frontier Foundation HDTV-PVR Cookbook
This opportunity ends July 1, 2005 for US residents!
The EFF HDTV-PVR Cookbook describes how to make your own "Tivo" like device to record television received via antenna.
...recent regulations in the United States will ban the manufacture of DTV-receiving hardware described here after July 1, 2005...despite the manufacturing ban, existing equipment will continue to work (and to be lawful to possess and operate); it will be immune from the restrictions imposed on future equipment. That means that the equipment you can buy today is more functional and more useful than what you may be able to buy after July 1, 2005.It is important to note that "this equipment does not receive satellite television of any kind, nor does it receive encrypted digital cable."
Some other pages of interest:
Thursday, March 24, 2005
What is PageRank and why is Google's ranking important?
Reprinted from Spy Journal Blog Tips:
PageRank™, named for Google's Larry Page who helped Sergey Brin develop the system at Stanford University, is an exclusive technology of Google which evaluates the popularity of your Website's pages by rating it between 0 and 10 with zero being little to no links to your site and 10 being Google (super, ultra, heavily linked).
Google shows PageRank for each visited site on its freely available Google Toolbar. For Firefox, Mozilla, and Netscape® 7.x users Google encourages installing the open-source Googlebar (not sure if this one shows page rank). There is also an extension for FireFox called Google Pankrank Status which will display the pagerank for the website you are visiting in your browser's status bar.
If you are adverse to installing a toolbar or extension to get the pagerank, some sites such as MyPageRank will report the ranking for you.
Why is PageRank important? Pagerank partly determines your placement in Google's results. Google's technology overview assures "human tampering with our results extremely difficult" and "no one can buy a higher PageRank." MyNippon on eBusiness blog advises to concentrate on good content and good products.
PageRank is heavily biased in favor of already popular web pages by making them even more popular (since they get found more often, they get linked more often). So what happens is that some websites continue to have low PageRank even if they have better content and new pages (with excellent content) may never be found in a search.MyNippon further recommends marketing your website. Companies like Superior Internet Designs can be contracted for Search Engine Optimization (SEO).
Some companies such as Adagio Teas view PankRank so important that they give away free product to increase their pagerank. Be aware that if you post your link to Adagio Teas in a post rather than in a permantently viewable part of your page they will only send you 1 tea. Read about Cathy's experience, Catawampus, and Zero Boss.
Mark Maughan viewed PageRank so importantly that he sued Google. (a clearer picture)
Peter Surna in June of 2003 showed us the numbers behind Google's PageRank and decried PageRank as useless unless you are writing an Internet search engine.
I close leaving the importance of PageRank for you to decide. I know two things. One, the higher my pagerank the more tea I'll receive; and two, this post helped several people's pagerank (create links whenever you can!).
Tuesday, March 22, 2005
The Internet Has No Security Architecture: Public Key Infrastructure And The Road To Secure Online Spaces
Robin Good posts a thought provoking piece of writing about internet security (or the lack of it). In fact he suggests that the notion of internet security is not possible to achieve in the current environment. Here's an example:
If you were a bank president and woke up one fine day to realize your bank had a secure vault door but no building around it, who would you call? A bank vault door technician? You'd call an architect, wouldn't you? You'd say, "Please start designing a building! When you're done I will give the plans to a contractor, and only after the contractor is on board will the two of you start contacting the vendors of sheet rock and framing materials and door locks and alarm systems and vault doors."
In other words the idea of trying to secure an open space with a vault door as is ridiculous as trying to secure your pc on the internet using the current tools; firewalls, virus and malware sweepers and the like.
The architectural approach begins with something called Public Key Infrastructure (PKI).
Read the full article to see how this remarkable tool could be used to help us design (architect) internet solutions that can provide security if the right professions get involved together.
Monday, March 21, 2005
The power of Amazon web services

Amazon Web Services (AWS) provides software developers direct access to Amazon's ever-growing technology platform and product data. Developers are empowered to innovate and build businesses by creating dynamic, highly-effective Web sites and Web applications.As demonstrated on Amazon's featured developer some companies like Monsoon LLC have made a business out of developing ecommerce sites based upon Amazon web services for business. To further show the possibilites, Amazon has some sample applications.
Showing prowess in creativity, Keita Kitamura and Yugo Nakamura created a fun tool called AmazType for Tha, LTD that uses Amazon web services to write words using book covers.

It appears that "spy journal" is primarily made up of this cover:
While "Tech Tips" uses these covers:
and more...
Sunday, March 20, 2005
UN backs cloning ban
The majority of member states in the United Nations General Assembly recently agreed to a non-binding ban on all forms of human cloning. In effect, this is merely a recommendation that will no doubt be ignored by nations who have already passed legislation approving the 'creation' of human beings for research purposes, such as Britain, China and Belgium, among others. Sadly, the British government has also already allocated two billion dollars (US) for embryonic stem cell research over the next ten years.
Much misinformation has been generated on this issue, particularly by organizations with vested financial interests. The fact that the UN now openly opposes cloning is a great opportunity to engage our leaders and encourage them to get on board. For clear, concise information on the issues of cloning and stem cells that you can share around, read Cloning: Right or Wrong? by information scientist Dr Werner Gitt, and
First human embryo clone? and Stem cells and Genesis by AiG's Dr Jonathan Sarfati.
Thanks to AIG for the news.
Wednesday, March 16, 2005
Irfanview, Photoshop and other tools
I just can't go past Photoshop for its amazing flexibility. I use it for nearly all my photo and graphic editing (not that I'm very good mind you.) For example the graphics on this site and the photo of the sun peeking through the clouds were all edited in Photoshop 5.
However for bulk file conversion and renames I use Irfanview.
The batch processing / conversion function is amazing. I use the advanced options to resize all the photos in a directory and create new files with the same name and a suffix to indicate their new size.
That way I can bulk process a whole raft of photos ready for upload to an online image gallery.
It is so easy to use that today I talked an international client through it on the phone in about 5 minutes flat. Within a second 5 minutes she had used an ftp program for the first time (Cute FTP PRO) and uploaded files to a Drupal website where they were converted into an image gallery using imagemagick which resides on my server.
Go and download Irfanview - its freeware and give it a try.
Sunday, March 13, 2005
Just what can this Internet thing do? Weather? Astronmy?
You know the sun rises. Did you know there is a moonrise? What to know what time the moon rises or sets? Just check The US Naval Observatory!
You can obtain the times of sunrise, sunset, moonrise, moonset, transits of the Sun and Moon, and the beginning and end of civil twilight, along with information on the Moon's phase [for any date anywhere in the world].
Friday, March 11, 2005
Document! Document! Document! (on paper)
Part I
As a programmer I've said it myself, "I don't have time to document my code."What we are really saying is "I did a poor job on this project."
Programming should begin with documentation. The IEEE has all sorts of documentation procedures and best practices (wow! An excellent short article by IBM). My first documentation happens when I meet with my client for the first time. I take notes and lots of them. I like to put each client/project into its own Mead Marble Composition Note Book. These are inexpensive, the pages don't tear out, notes are storied chronologically, they fit neatly in a file cabinet and stand out amongst the junk on your desk. I also keep a file folder with the note book for all loose papers and printouts.
The first note I collect from the client is contact information. This is documentation! If another programmer picks up your project that programmer needs to know who to contact. Imagine this scenerio:
President of the company Alice assigns manager Sue to hire Superior Internet Designs to build a piece of software. SIDesigns assigns programmer Joe to the job. Programmer Joe gets hit by a bus. SIDesigns offers to put programmer Beth on the job but president Alice decides her employees are all too busy at the time and delays the project. Six months later president Alice contacts SIDesigns to say she has assigned manager George to see this project through and programmer Beth is placed on the project.Without documentation George and Beth would effectively be starting over. If the contact information had been documented, Beth would know to ask if manager Sue was available to bring them up to speed on the project.
Example 1
Back to my initial meeting with a client. After recording contact information, I let my client describe their needs. I try hard to listen and avoid talking. At this point I am trying to learn what they want done and if I contribute too many "what ifs" or "you could do" statements then I am leading them and we will likely develop a product that doesn't match their initial expectations. While the client talks I am documenting. In my notebook I record as much as I can of what the client says. These notes will later be refined into a formal requirements document. Ludwig Consulting Services, LLC has some excellent document templates. Their documentation is closer to the level of documentation used on government projects. Unless your have an exoberant budget for documentation I recommend you use the concepts and simplify the documentation.
After the client is done describing their needs I will ask some pointed questions and record those answers in my notebook. When the meeting is done I will immediately transcribe my notes into an electronic form creating a specification document and requirements document.
All documentation must go through a client review!
We will continue in another post and discuss recording assumptions, data diagrams and data dictionaries.
Thursday, March 10, 2005
Toshiba and generation Y big technology spenders
Lifted from the Bleeding Edge Web site - an excellent technical site (with some off beat quirky satire thrown in!)
Bleeding Edge spent today at Toshiba's Mobile Xchange conference - an event dedicated to the proposition that if a lot more Australians were engaged in flexible work practices, which is what we used to call tele-working or tele-commuting - Toshiba would sell a lot more portable computers.
For all that, however, it produced some interesting facts and theories, among them the fact that while Australia might be ageing, in fact Generation X and Y (23 to 40-year-olds and 5 to 22-year-olds) outnumber Baby Boomers (26 per cent) and their parents, aka "Builders" (17 per cent), which means technology companies are going to have a lot more customers for new toys than they ever had in the past.
Indeed companies like Toshiba feel positively giddy with joy at the prospect of Generation Y getting older and earning more money, because they've never seen a demographic that's more determined to deploy their credit cards and overdrafts in the pursuit of gadgets.
As social researcher Mark McCrindle put it, this most digitally literate demographic buys technology not just because of their work or entertainment needs, but also because they regard it as a fashion item.
Their entire social standing is apparently dependent on their ability to buy and use mobile phones and digital cameras and PDAs and MP3 players, etc.
Apparently they can sicken and die if they're caught using technology that's not classified as acceptable (ie, slightly out of date).
What's particularly dangerous, as far as the rest of us are concerned, is that they are apparently spreading this disease to their parents, friends, and indeed anyone they come in contact with. They are carriers, God help us, of consumerism.
There's even an International Journal of Advertising and Marketing to Children, which studies their behaviour. They call them "kidults", and their wallet-loosening powers as "kidfluence".
When you think of it, they're probably a national calamity, given that they're probably the ones who are driving our current spending binge.
Bleeding Edge's advice, if you happen to have contact with this generation - you'll probably be able to recognise them by the fact that they have white earphones attached to their heads - is to have them humanely put down. We don't really mean that, of course. Just don't talk to them. And don't let them near your credit cards.
Friday, March 04, 2005
Windows XP SP2 Deployment guide
More searching the huge Microsoft.com Website led me to a Windows XP Service Pack 2 Deployment Information page.
(written 27 November 2004 and not posted until now)
Feedfire
I use Feedfire to create RSS feeds for websites that haven't got an XML link on their site.
So far it has worked for every site I have tried.
Create a login and try it - it works great.
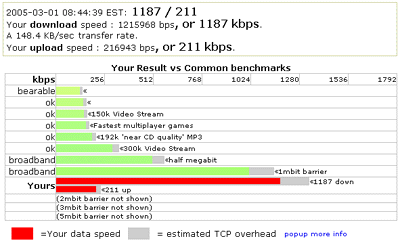
Tuesday, March 01, 2005
Upgraded Broadband Speed
I have just upgraded my ADSL Connection to 1500/256.
There is a noticeable difference in download speed.
I hope it will also reduce the load I had on the server in recent months as traffic to the various sites we host has increased somewhat.
In fact I have had to move the SpyJournal sites off to a colo server. They are getting about 4.000 site hits a month now and growing all the time.
Here is a pic of the speed as tested with the ISP.